Ma Xianming, Shenzhen Yanxiang Intelligent Technology Co., Ltd.
Keywords: domestic processor Godson; secure interconnection equipment; information security
0 Preface
The widespread use of IP protocol devices in Industrial Control System (ICS) applications has reduced system development, operation, maintenance, upgrade, and networking costs, and has greatly promoted industrial production; With the use of general-purpose computers and network technologies, the number of information security issues is increasing, and the threshold for damage from cyber attacks has been gradually reduced.
Figure 1 shows the architecture of a traditional industrial control system. The Industrial Numerical Control (DNC) numerical control network system is responsible for data acquisition, digital-to-analog conversion, device control, and manufacturing through configuration and design.
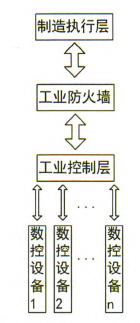
Figure 1 Traditional Industrial Control System Architecture
Simple boundary isolation and access control are often performed only between firewalls in the manufacturing execution layer and industrial control layer (DNC numerical control network system), and the technical measures for security protection at the industrial control layer management terminal are very weak. Between the manufacturing execution layer and the industrial control layer Access and communication can be performed through various ports and protocols. Attacks such as viruses, Trojans, malicious code, and hackers can easily use these security vulnerabilities, occur on the terminal, initiate, and infect or damage the industrial control layer system through the network.
Because there are many types of CNC machine tools, a variety of communication interfaces, a variety of general purpose or special operating systems in the industrial control layer system, there are different types of information interaction between the industrial control layer and the manufacturing execution layer. The security of information exchange is difficult to detect. Whether it is industrial-grade firewalls or network isolation gateways, it is impossible for security risks and threats such as Trojans, viruses, and network attacks that may cause information disclosure and control instructions to be tampered with in DNC numerical control network systems.
The operating system of numerical control equipment in the industrial control layer mostly uses dedicated operating systems, including the FANUC system (Frank), SIEMENS (Siemens), Fidia (Fidia), etc. Only a few numerical control devices use general operating systems such as Windows NT and Windows XP. Most of the NC processing equipment backstage have no windows operating system. At the same time, because the underlying code of these dedicated operating systems is not open, its function is not fully understood. The behavior of production equipment in the industrial control layer is a proprietary specific behavior, and the behavior of different production equipment is different. It is necessary to scientifically analyze and evaluate the behavior of the production equipment of the industrial control layer system, and it is very difficult to realize the safety audit of the production equipment. Big. Compared with the malicious code detection and stripping technologies of general operating systems such as Windows and Linux, the security profile analysis, vulnerability analysis technology, and malicious code detection for the dedicated operating systems such as FANUC, SIEMENS, Fidia, etc. are still in the preliminary stage. The virus detection system and the malicious code detection tool cannot detect malicious behaviors of the dedicated operating system for CNC equipment.
Traditional firewalls cannot effectively detect malicious behaviors against numerical control devices because industrial firewalls are general-purpose computer devices. The numerical control devices in the industrial control layer are special-purpose devices, not general-purpose computer devices. The malicious code for numerical control devices is only for digital control. The equipment is effective and produces malicious behavior without any impact on general-purpose computer equipment. Therefore, industrial firewalls cannot detect malicious code for CNC equipment.
It is therefore necessary to design a secure interconnection device in the industrial control layer to improve the safety of industrial production.
1 Overall design
Loongson 2H is the successor to the domestic processor Godson 2 series. Its goal is to provide a single-chip solution for safety-compliant computers. Godson 2H is implemented in a 65nm process, with a frequency of 1GHz or more, a power consumption of less than 6 watts, and a high-performance power ratio. On-chip integrated fixed-point processor, floating-point processor, streaming media processing and graphic image processing functions, and supporting chipset functions such as Southbridge and Northbridge.
The domestic Godson-2H processor, as an autonomous and controllable processor in China, ensures the safety of the processor and avoids the loopholes and backdoors at the key chip level. The use of the Godson-2H processor as a hardware platform for secure interconnection devices ensures the security of the hardware design and prevents the security impact due to uncontrollable core components (processors).
Figure 2 shows the architecture of an industrial control system after adding secure interconnected devices. The safety interconnection equipment based on the domestic Godson-2H processor design will receive the production data passed through the industrial firewall and detect the malicious code specially designed for CNC equipment. The malicious code detected by the safety interconnection equipment will illegally operate the CNC equipment production. Malicious code will not cause any abnormal impact on general-purpose computers. Therefore, traditional industrial firewalls cannot detect these malicious codes specifically for numerical control devices. It is necessary to introduce secure interconnected devices designed based on the domestic Loongson 2H processor to detect and process malicious code.
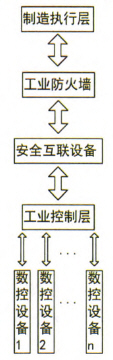
Figure 2 Industrial Control System Architecture after Joining Security Interconnected Equipment
2 Hardware Design
The domestic Godson 2H processor has the following key features:
(1) Integrate a GS464 four launcher Loongson processor core
(2) Integrates a 64-bit DDR2/3 controller
(3) Integrated PCIE gen2 controller supporting 1x4 and 4x1
(4) Integrated 2 10M/100M/1000M adaptive GMAC
(5) Integrated 2 SATA2
The secure interconnection equipment based on the domestic Godson-2H processor design puts forward high-speed, reliable and intelligent requirements for product design. In addition to the high performance of the core processor of the secure connected device, it requires an operating system with high real-time performance and stability, and it also needs to have a 64-bit high-performance processor to guarantee the implementation of the algorithm. In the high-performance general-purpose processor, the domestic Godson-2H processor has reached a relatively high processing performance and meet the requirements of multi-tasking.
The Godson 2H processor has a high degree of integration, provides rich functional interfaces, high performance, low power consumption, and is fully autonomous and controllable, meeting the configuration requirements of secure interconnected devices, and its superior single-chip solution replacing traditional processors plus North and South Bridges. The design scheme will greatly simplify the design of the hardware circuit, avoid the complexity and technical difficulties of the logic circuit design, reduce the difficulty of the electromagnetic anti-jamming design, greatly shorten the development cycle, and accelerate the time for the company to market the safety interconnection equipment. The Godson 2H processor-based security interconnection device is shown in Figure 3.
Figure 3 Based on Loongson 2H processor security interconnection equipment
3 Software Design
Figure 4 shows the software processing flow for secure interconnected devices. The safety interconnection equipment based on Loongson 2H processor receives malicious code detection, reliable behavior detection, and reliable data detection after receiving production data that needs CNC equipment to produce. Only after all tests are normal can production data be sent to the industrial control layer. The CNC equipment is used for production. Otherwise, the detected production data will be discarded, alarmed, etc., and the production data containing malicious code will be rejected from the CNC equipment.
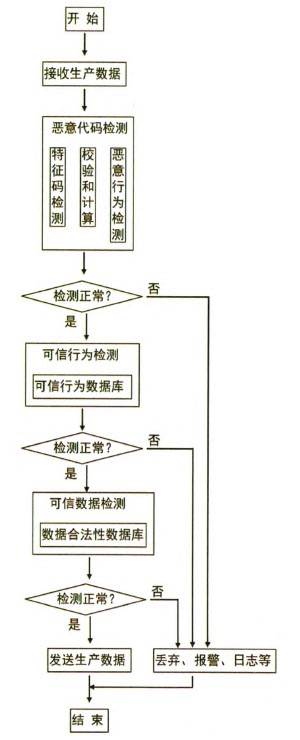
Figure 4 software interconnection process
The safe interconnection device based on Loongson 2H processor needs to perform malicious code detection after receiving production data from an industrial firewall. The malicious code detection function is mainly to prevent malicious code in the manufacturing execution layer network from intruding into the industrial control layer network.
Malicious code detection can be implemented using signature detection, checksum calculation, and malicious behavior detection techniques.
Signature detection is the most widely used and most widely used detection method. By analyzing a large number of infected files that once caused malicious behavior to CNC equipment, the malicious code features for numerical control devices are summarized to obtain the signature of the obtained malicious code. Based on the Godson 2H processor's secure interconnection device, the production data is scanned in bytes and the production data is compared with the signature of the malicious code. If the detection result matches the malicious code signature, the malicious code detection is abnormal, indicating that the detected production data contains malicious code that is dangerous to the numerical control equipment; if the detection result does not match the malicious code signature code, the malicious code detection result is normal, indicating that the detected The production data does not contain malicious code that is dangerous to CNC equipment.
The checksum calculation is based on the production data information before production data is generated at the manufacturing execution layer, including the file name, size, time, date, and content. The checksum is calculated and the checksum value is written into a file or written to another file. Save it. The file containing the checksum value is sent to the secure interconnected device along with the production data. The secure interconnected device recalculates the checksum value based on the existing information of the file and the checksum value originally saved in the file and compares them to see if the result is consistent. . If the checksum value is inconsistent by comparison, it means that the production data already contains malicious code, and the production data cannot be sent to the numerical control equipment for production, indicating that the malicious code detection result is abnormal; if the checksum value is compared, the values ​​are consistent. , then the production data is normal, no malicious code, the production data can be used for numerical control equipment for production, indicating that the malicious code detection results are normal.
Malicious behavior detection is a method that uses malicious code's unique behavior features to detect malicious code. In general, some behaviors of malicious code are the common behavior of malicious code, and they are special. In normal production data, these behaviors are rare and unlikely to occur in normal production data. By analyzing a large number of infected files that once had malicious behavior on CNC equipment, the malicious behavior characteristics of malicious code were summarized to form malicious behavior signatures. The malicious behaviors of production data include misappropriation of the cutoff system, modification of the total amount of memory and memory control blocks, and write operations to executable files. If the secure interconnected device detects the behavior of the production data, if a malicious behavior signature is found, the malicious code detection result is abnormal. If no malicious behavior signature is found, the malicious code detection result is normal.
When malicious code detection is abnormal, it means that the detected production data contains malicious code and cannot be used for numerical control equipment. The detected production data needs to be discarded, alarmed, and written into log information. If the detection of malicious code is normal, it means that the detected production data does not contain malicious code and needs to conduct a credible behavior detection.
The credible behavior detection is the analysis of the business logic and operating procedures of the industrial control system by analyzing a large number of documents that are valid and correct for the numerical control equipment, and summarize the credible behavior code characteristics for the numerical control equipment. Trust the signature of behavior detection and establish a database of trusted behaviors. Trusted behavior of CNC equipment includes rotation, upward movement, downward movement, leftward movement, and rightward movement. Stored in the credible behavior database are the signatures of the correct behavior of CNC equipment. Only the behavioral operation code stored in the credible behavior database is the correct behavior. Otherwise, it will be deemed as incorrect behavior, which can improve the discovery industry. The control system is unknown for the possibility of attack threats. The secure interconnection device scans the production data in bytes and compares the production data with the trusted behavior signature stored in the trusted behavior database. If the detection result does not match the trusted behavior signature, it indicates that the trusted behavior detection is abnormal, indicating that the detected production data contains malicious code that is dangerous to the numerical control equipment. The detected production data needs to be discarded, alarmed, and written into log information. If the test result is consistent with the credible behavior signature, it means that the credible behavior detection result is normal, indicating that the detected production data does not contain malicious code that is dangerous to the numerical control equipment. The detected production data is consistent with the credible behavior of the numerical control equipment. The correct data for the operation.
Then the need for reliable data detection, trusted data detection is to analyze and summarize the legal operating range of the credible behavior in a large number of production data, and establish a data legality database. The credible data of CNC equipment includes the minimum and maximum rotation angles. , the minimum and maximum distances to move up, the minimum and maximum distances to move down, the minimum and maximum distances to the left, the minimum and maximum distances to the right, and more. The secure interconnection device scans and detects the credible behavior data of the production data, and compares whether the credible behavior data of the production data is legal, that is, whether it is between the minimum value and the maximum value of the credible behavior specified in the data legality database. If the reliable data detection is normal, it means that the detected production data does not contain any malicious code that is dangerous to the numerical control equipment. The detected production data meets the requirements of numerical control equipment production. If the trusted data is detected abnormally, it means that the detected production data contains illegal data that exceeds the normal operation of the trusted behavior. The detected production data needs to be discarded, alarmed, and written into log information.
If the detected production data can be normally detected by the safe interconnection device, then the production data does not contain any malicious code that affects the numerical control device. The data can be sent to the industrial control layer for secure production via the secure interconnection device.
4 Conclusion
This paper proposes a secure interconnected device based on Loongson 2H processor, and adopts techniques such as malicious code detection, trusted behavior detection, and trusted data detection for malicious code and malicious behavior that may exist on numerical control devices, thereby improving the security of industrial control systems. .
500 Portable Power Station,Lifepo4 Portable Power Station,Economical Portable Solar Power Station,Portable Power Station For Camping 500W
Jiangsu Zhitai New Energy Technology Co.,Ltd , https://www.zttall.com