How do you use these elements in combination with multiple Internet technologies for IoT systems that use sensors and maintain connectivity?
Internet protocols are no strangers, but Internet protocols related to IoT may be different, and some protocols are used to help shape the system. There are multiple application layer protocols on the TCP/IP stack. Each has its own advantages and limitations. Understanding these can help developers make the best design choices for their products. When choosing an IoT protocol, bandwidth requirements, real-time performance, and memory footprint are the main constraints.
Given the diversity and complexity of IoT, there are many types of application scenarios:
Consumer versus industrial Consumer vs industrial
Web services web services
IoT services IoT services
Publish/subscribe publish/subscribe
Request/response request/response
. . . . . .
When designing an IoT system, these categories must be considered, and clear requirements and boundary determination are almost the key to success. In general, an IoT system is roughly the same:
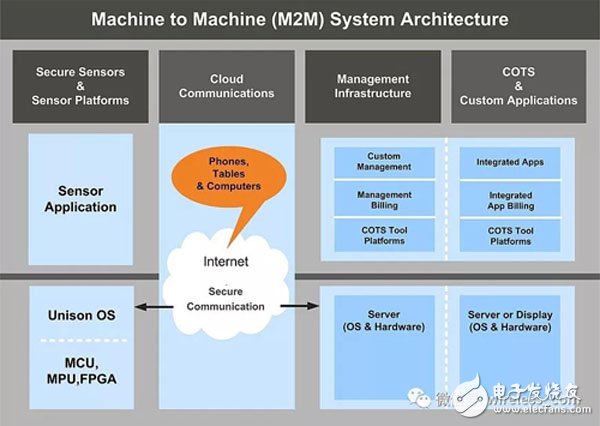
Figure 1 General system architecture of IoT (M2M)
The interface-oriented design is widely accepted by the industry and extends to the system level. It is about protocol-oriented design, and the understanding of the protocol is the basis of the design.
Internet protocol stackThe Internet is the sum of all network devices used to route IP packets from the source to the destination. In contrast, the Web is just an application system that runs on the Internet. The Internet is a communication tool. In the past few decades, the Internet has been popularized and developed, and ordinary people can use the Internet easily and effectively. For example, email, search engines, browsers, mobile apps, and other popular social media.
In contrast, the Internet of Things is for electronic devices to exchange information over the Internet. But these devices don't promote communication like browsers and social media. The Internet of Things is also different from the Internet. Because the speed, scale, and functions required by IoT devices to work together are different from those of the Internet, the demand is varied. This is one of the reasons why the definition of the Internet of Things is difficult to be clear.
The protocol stack is the core of the Internet and the network. It is inseparable from the representation of the OSI seven-layer open system interconnection. For details, please refer to the network programming foundation of Lao Cao. Here, the top three layers are grouped together to simplify the model.
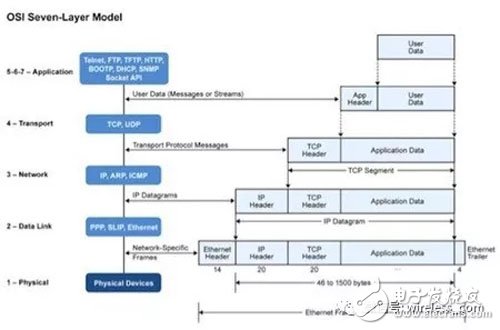
Figure 2 Summary of the OSI model
We need to quickly understand the OSI layer from the perspective of IoT.
The next three layers: physical layer, data link layer, and network layer
The physical layer and data link layer protocols commonly used in the Internet are:
Ethernet (10 Mbps, 100 Mbps, 1 Gbps)
Wi-Fi (802.11b/g/n)
Point-to-Point Protocol (PPP)
GSM, 3G, 4G, LTE 3G, 4G, LTE
However, for IoT, the wireless protocols used are more abundant, such as 802.15.*, and even the related protocols of the metropolitan area network and other WANs have been introduced, and the latter is separately understood.
The network layer is where the Internet survives. The Internet is named because it provides connectivity between networks and between physical layers. This is where we find the ubiquitous IP address.
Transport layerOn top of IP, the Internet has two transport protocols - TCP and UDP. TCP is used for interactions in the network (email, web browsing, etc.) and is even considered to be the only protocol in the transport layer. TCP provides the concept of logical connections, acknowledgment of transport packets, loss of lost packets, and flow control. But for IoT systems, TCP can be a bit heavy. Therefore, although UDP has long been downgraded to network services such as DNS and DHCP, it has now taken a place in the field of sensor acquisition and remote control. If you need to manage some type of data, you can even write your own lightweight protocol on top of UDP to avoid TCP overhead.
For real-time data applications such as voice and video, UDP may be more suitable than TCP. TCP packet acknowledgment and retransmission capabilities may be useless overhead for these applications. If a piece of data (such as a piece of spoken audio) does not arrive at the destination in time, retransmission of the packet may not be significant. TCP is sometimes chosen because it provides a persistent connection. In order to achieve similar functionality, this feature must be implemented in the protocol layer above UDP.
When deciding how to move data from a "things" local network to an IP network, you can connect the two networks through a gateway, or you can build this functionality on the "things" itself. Many microcontrollers (MCUs) now have an Ethernet controller, which makes this task easier.
Wireless protocol for the Internet of ThingsWhile most IoT relies on traditional embedded development techniques, there is always a need for connectivity, which requires us not only to make choices about wireless methods, but also to choose the appropriate communication protocol. Therefore, different protocols are attempting to establish the basis for providing data communication from edge nodes to cloud services. Each protocol is expected to be considered the best choice for some type of data or data exchange method.
IoT wireless protocol evolved from computer networksNest Labs used the Thread Group agreement in smart thermostats and smoke detector products, which was acquired by Google in 2015 and has grown rapidly. As partners and user communities continue to grow, the potential of the Thread Group makes it a viable alternative to technologies such as ZigBee, Z-Wave and Bluetooth Low Energy (BLE). The main reason for its success is that Google did not develop a new protocol, but built it based on the IEEE 802.15.4 wireless standard.
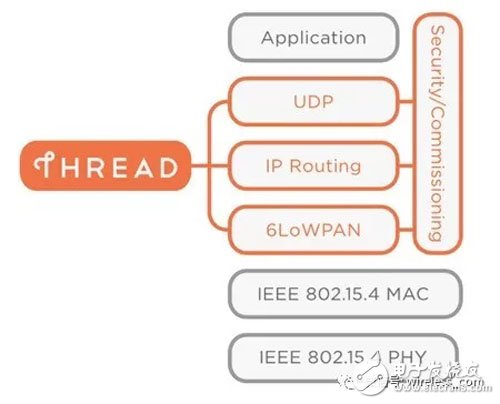
Figure 3 The main components of the Thread protocol
The Thread Group's goals are home appliances, access and climate control, energy management, lighting, security and more.
BLE may be the biggest competitor of the Thread Group, but BLE is not yet a self-healing network, and this network is becoming a prerequisite for IoT applications. Reliability is the key to any form of communication based on sensors, such as thermostats, safety alarms, and of course for safety-first industrial applications. Despite this, BLE certainly has not quit the IoT protocol competition. Benefiting from years of enhanced functionality, some Bluetooth Technology Alliance (Bluetooth SIG) participants, such as Broadcom, Qualcomm and other industry leaders, are working to improve BLE's capabilities for IoT applications.
The Bluetooth SIG also paved the way for connecting the Internet with the launch of the Bluetooth Intelligent Network Working Group (currently more than 80 companies support the working group) with the goal of establishing a standardized Bluetooth network network architecture.
IPv6, IEEE 802.15.4, and a personal area network called IPv6 are complementary to the low-power wireless personal area network (6LoWPAN) used by Thread Group, ZigBee, and Z-Wave because the latter two networks are clear A device with limited processing power, low data rate, extremely low RF output power, and extremely low power or battery power consumption. This will make equipment and network design relatively simple and cost effective.
Due to the low latency of Thread (usually 100 milliseconds, typically less than Wi-Fi), it can accommodate up to 300 devices on a network, providing AES 128-bit security, and a mesh network approach. Targeted as a protocol suitable for use in IoT applications. However, there is no evidence that Thread will be the leader in IoT connectivity. As the Internet of Things grows, many protocols obviously have to build their own space, perhaps identifying their location in a particular application.
Long distance IoT wireless protocolLPWAN technology is a long-distance wireless communication technology that meets the needs of the Internet of Things.
For telecom operators, IoT applications such as car networking, smart healthcare, and smart home will generate massive connections, far exceeding the communication needs between people. The Narrow Band Internet of Things (NB-IoT) is an important branch of the Internet of Everything. Built on a cellular network, NB-IoT consumes only about 180KHz of bandwidth and can be deployed directly on GSM networks, UMTS networks or LTE networks to reduce deployment costs and achieve smooth upgrades.
Focusing on the Low Power Wide Coverage (LPWA) Internet of Things (IoT) market, NB-IOT is an emerging technology that can be used globally. It has the characteristics of wide coverage, many connections, low speed, low cost, low power consumption and excellent architecture. The NB-IOT uses the licensed frequency band and can adopt three deployment modes: in-band, guard band or independent carrier to coexist with the existing network.
Domestic Huawei is more effective on NB-IoT. The end-to-end solution given by the company is as follows:
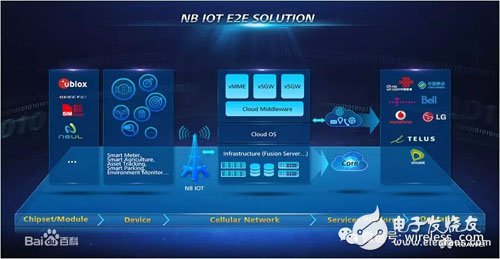
Figure 4 NB-IoT E2E soluTIon
In the unlicensed band, there are also related wireless protocols for IoT. Corresponding to NB-IoT, the protocols of LP-WAN in the unlicensed spectrum mainly include LoRa, SigFox and other technologies. The network deployment topology layout can be designed according to the specific application and scenario. For example, LoRa is suitable for applications with low communication frequency and low data volume.
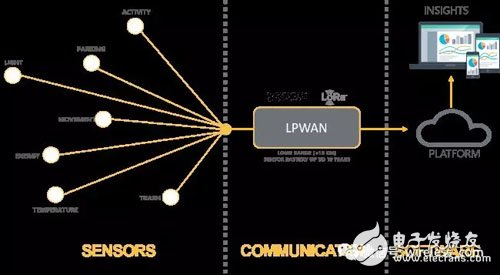
Figure 5 LPWAN solution
Other common protocolsSo what are the agreements for zigbee / zigbee Pro, Z-Wave, AllJoyn, CSR Mesh, and IoTIvity?
Operating at 2.4 GHz and with a maximum data rate of 250 gigabits, Zigbee 3.0 has been widely supported by approximately 400 vendors and can support thousands of nodes using a comprehensive network protocol. It has a link distance of approximately 100 feet, supports IPv6, and provides 128-bit AES encryption security. This latest release includes all of the past ZigBee application configurations, and the ZigBee Alliance has been criticized.
Like ZigBee, ZigBee Pro is a relatively new specification. This mesh network protocol is clearly optimized for the Internet of Things. It can operate not only on the 2.4 GHz spectrum, but also in the 800-900 MHz unlicensed spectrum. With spread-spectrum modulation, there are more than 16 channels, in addition to broadcast transmission options, star-shaped topologies are also supported. As with most IoT node applications, energy conservation is a primary consideration, so protocols meet battery-free devices that harvest energy through a variety of electromechanical, optical, or motion methods.
At the same time, Z-Wave operates only in the 800-900 MHz band and is still supported by more than 375 organizations.
Within the Linux Foundation, there is the AllSeen Alliance with the AllJoyn framework. Alljoyn is an open source, collaborative software framework that allows developers to write applications for the Internet of Things, regardless of brand, category, transmission medium and operating system, to write applications for the Internet of Things without the need for cloud computing or even the Internet ( But both are supported). It supports Wi-Fi, Ethernet, serial ports and even power line transmission media. Supported operating systems include RTOS, Arduino, Linux, Android, iOS, Windows and Mac. The framework also uses 128-bit AES encryption and is currently supported by more than 120 companies.
Another protocol that runs inside the Linux Foundation is IoTIvity, which focuses on improving interoperability and defining the connectivity needs of the Internet of Things. It uses a common communications framework to manage the flow of information between personal computers and emerging IoT devices, regardless of form factors, operating systems or service providers.
Internet high-level protocol that can be applied in the Internet of ThingsAlthough not as effective as the new protocol, it is still possible to build an IoT system using web technology. Http/https and websocket are common standards, as well as XML or JSON in the payload.
HTTP
Http is the foundation of the web client-server model. The safest and simple way to implement HTTP in an IoT device is to include only one client, not the server. In other words, when an IoT device can initiate a connection to a network server but cannot receive a connection request, it is more secure; it is generally undesirable for an external machine to access the local network with the IoT device.
WebSocket
Websocket is a protocol that provides full-duplex communication over a single TCP connection, through which messages can be sent between the client and the server. It is part of the HTML5 specification. The Websocket standard simplifies most of the complexity of two-way network communication and connection management.
XMPP
XMPP is a good example of the application of existing web technologies in the Internet of Things. Xmpp is rooted in instant messaging and stored information, and has been extended to generalized routing of voice and video calls, collaboration, lightweight middleware, content aggregation, and XML data. It can manage consumer products on a large scale, such as washing machines, dryers, refrigerators, and more.
The advantages of XMPP are address, security, and scalability, making it a good choice for consumer IoT applications.
HTTP, WebSocket, and XMPP are just a few examples, and many organizations are working hard to find solutions to the new IoT challenges.
High-level protocol for the Internet of ThingsMany IoT experts refer to IoT devices as restricted systems because IoT devices should be as cheap as possible, and run the protocol stack while using the smallest capable MCU.
If the system does not require TCP features and can use more limited UDP functionality, then removing the TCP module will greatly reduce the total code size of the product, which is the application of 6LoWPAN and CoAP in the Internet of Things.
CoAP
While network infrastructure is available for IoT devices, it is still too heavy for most IoT applications. In July 2013, the IETF released CoAP for low-power node networks. Like HTTP, CoAP also has the ability to RESTful operational resources and resource identifiers.
CoAP is aligned with HTTP semantics and even has a one-to-one HTTP mapping. Network devices are constrained by smaller MCUs with only a small amount of flash and RAM, while local network limitations are high packet error rates and low throughput (tens of kb/sec). CoAP is a good protocol for devices running on batteries or energy harvesting components.
Features of CoAP:
Since CoAP uses UDP, some TCP functions are copied directly in CoAP. For example, CoAP distinguishes between identifiable (requires confirmation) and non-acknowledgement messages.
Requests and responses are asynchronously exchanged on CoAP messages (unlike HTTP using existing TCP connections)
All headers, methods, and status codes are binary coded, which reduces protocol overhead. However, this requires the use of a protocol analyzer to debug network problems.
Fully considering that this is an extremely minor protocol that behaves like a permanent connection. It is very similar to HTTP semantics and is RESTful. If you have a background in network programming, it is relatively easy to use CoAP.
MQTT
MQTT is an open source protocol developed and optimized for restricted devices and low bandwidth, high latency or unreliable networks. It is a publish/subscribe transport model that is very lightweight and ideal for connecting small devices to networks with low bandwidth. MQTT is bandwidth efficient, data agnostic, and has continuous session intent when using TCP. The aim is to minimize the resources required for the equipment while working to ensure the reliability of the service level and to some degree of assurance.
The goal of MQTT is a large network of small devices that need to be monitored on the back-end servers of the Internet. It is not designed for inter-device transmission, nor is it designed for "multicast" data for many receivers. Applications that use MQTT are sometimes slow, because in this case, the definition of "real time" is usually measured in seconds.
A brief comparison of MQTT and CoAPThe release/subscription model of MQTT is very good, and the advantages of this architecture have been proven. In the latest RFC of the IETF, CoAP introduced support for publish/subscribe. CoAP's lightweight payload is ideal for wireless sensor networks. The sensor MQTT network has adopted and replicated this idea.
Two major IoT-specific protocols draw on each other. But are these two agreements mainstream? Time test is still required.
Choice of IoT protocolConnecting sensors and transaction objects opens up a whole new world that will determine when to use the protocol for the application.
The layer locations of these protocols are all similar. In addition to HTTP, all of these protocols are targeted to real-time publish/subscribe IoT protocols, supporting millions of devices. Depending on how you define "real time" (seconds, milliseconds or microseconds) and "things" (WSN nodes, multimedia devices, personal wearables, medical scanners, engine controls, etc.), the choice of protocol for the product is critical. Fundamentally, these agreements are very different.
When designing a system, what needs to be done is to define the system requirements very accurately and choose the right protocol to solve the problem. A network protocol is a carrier that encapsulates many protocols of the Internet of Things like the Web.
Once the protocol or set of protocols is deemed to meet the deployment, management, and support of the application, the best implementation of each protocol should be understood. In view of this, the design needs to choose the best implementation of each protocol for the system, and then choose the best protocol implementation of the system from these protocols.
The protocol selection problem is closely related to the implementation of the protocol, and the components supporting the protocol are often essential in the final design. This makes this decision very complicated. All aspects of deployment, operations, management, and security must be considered as the choice of protocol, including the implementation environment.
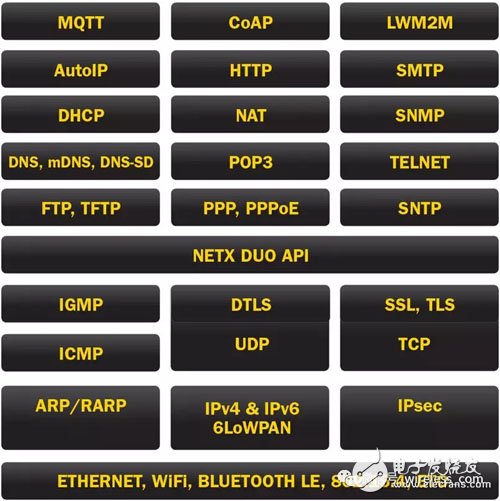
In order to meet the needs of IoT devices with low memory, low bandwidth and high latency, there are many Internet-facing Internet of Things protocols. Figure 6 provides another summary of the performance benefits these protocols bring to the IoT.
In addition, there are no uniform standards for specific applications, and these standards are usually chosen by the market. As a developer, using the specific characteristics of the environment to meet the requirements of the system, which in turn depends on the details of the protocol, it will become very difficult to deal with future changes.
The choice of the protocol stack and the relationship of the supplierThe advanced protocols of the Internet of Things have a variety of features that provide different capabilities. Most agreements are developed by specific vendors who typically promote their own protocol choices, do not explicitly define their assumptions, and ignore other alternatives. For this reason, relying on vendor information to select IoT protocols is problematic, and most of the comparisons that have been made are not sufficient to understand the trade-offs.
IoT protocols are often tied to business models. Sometimes these protocols are incomplete and/or used to support existing business models and methods. Sometimes they provide a more complete solution, but for smaller sensors, the resource requirements are unacceptable. In addition, the key assumptions behind the use of the protocol are not clearly stated, making it difficult to compare.
The basic assumptions of IoT applications are as follows:
Will use a variety of wireless connections
Devices range from micro-controllers to high-performance systems, with a focus on small MCUs
Safety is the core requirement
Data will be stored in the cloud and may be processed in the cloud
Need to connect to cloud storage
Need to transfer information to cloud storage over wireless and wired connections
Other assumptions require more in-depth investigations and will require a deeper understanding of their choices. By looking at the key features of these protocols and reviewing key implementation requirements, designers can more clearly understand what is needed in the area of ​​protocols and supporting features to improve their design.
Key features in protocol selection
IoT communication is based on the Internet tcp / udp protocol and related Internet protocols. For basic communication, this means either a TCP stream socket for UDP packets. Developers of small devices claim that UDP has a big advantage in terms of performance and size, which in turn reduces costs. Although this is true, in many cases it is not important.
Although Stream Sockets are affected by performance, they do guarantee an orderly transfer of all data. The performance of transmitting sensor data on the 167mhz STM32F4 was affected by less than 16.7% (measured with a 2kb packet). By adopting a stream socket approach, standard security protocols can also be used to simplify the environment (although DTLS can be used with UDP if available).
Similarly, the difference in memory cost for adding 20 KB of flash and 8 kb of memory to TCP is usually small. This can make sense for a large number of micro-applications and sensors, but it usually does not affect the design of the ARM Cortex-M3, nor does it affect other architectures such as RX, PIC32 and ARM Cortex-Ax.
Message model
The method of information transfer to the general Internet of Things is very important, and many protocols have been migrated to a publish/subscribe model. The publish/subscribe request/response model has advantages because many nodes are connected and disconnected, and these nodes need to connect to various applications in the cloud. It dynamically responds to random on/off operations and supports multiple nodes.
Both CoAP and HTTP are based on request response, and no publish/subscribe method (CoAP has been introduced in the new RFC). In the case of CoAP, automatic addresses using 6LoWPAN and IPv6 are used to uniquely identify nodes. In the HTTP example, this approach is different, because the request can be anything, including a publish request or a subscription request, so in fact, the design of this approach is general. Today, these protocols are combined to provide a complete publish/subscribe request/response model.
Topology architecture
The system architecture is diverse, including CS, tree or star, bus, and P2P. Most people use CS, but others use the bus and P2P methods. A star structure is a tree method. For these topologies, performance issues typically exist in P2P and bus architectures. Simulation or prototyping methods need to be adopted early in the design to prevent accidents.
Scalability
Scalability depends on adding multiple nodes to the field and adding cloud resources to serve these new nodes. Different architectures have different characteristics. For a client server architecture, it is easy to increase the pool of available servers. For bus and P2P architectures, scale is inherent in the architecture, but there is no cloud service. For architectures connected to trees or stars, there may be problems associated with adding extra leaves to the tree, which adds to the burden on the communication node.
Another aspect of scalability is dealing with a large number of constantly changing nodes and linking these nodes to cloud applications. As discussed, the publish/subscribe request/response system is designed for scalability because it needs to handle nodes that are offline for various reasons. These nodes allow applications to receive specific data when deciding to subscribe and request data, thus enabling fine data. flow control. The less robust method does not scale well.
Self-healing
Low-power and lossless networks are node-level moving. This dynamic behavior may affect the overall network, so the protocol is designed for multipath dynamic reconfiguration. The dynamic routing protocols found in ZigBee, ZigBee IP (using 6LoWPAN) and 6LoWPAN ensure network adaptability. Without these features, processing these nodes becomes a discontinuous operation, making the node's resource requirements higher.
Resource requirements
As the number of applications increases, resource requirements are key. The microcontroller handles the problems listed above at a very low cost. Some protocols are too resource intensive and do not apply to small nodes. Discontinuous operations and big data storage will be limited unless a large amount of flash memory or other storage media is included. As resources increase, in order to reduce the cost of the entire system, it may be necessary to add aggregation nodes to provide additional shared storage resources.
Interoperability
Interoperability is essential for most devices in the future. So far, a series of point solutions have been seen, but end users want sensors and devices to work together. By using a standardized set of protocols and standardized messages, devices can be separated from the cloud services that support them. This approach provides complete device interoperability. In addition, with the Smart Publish/Subscribe option, different devices can even use the same cloud service and offer different features. With an open approach, application standards will emerge, but not yet.
safety
Using a standard information security solution is the core security mechanism for most protocols that provide security. The basis of these security measures is:
TLS
PSec/VPN
SSH
SFTP
SecurebootloaderandautomaTIcfallback
Filtering
HTTPS
SNMPv3
Encryptionanddecryption
DTLS (forUDP-onlysecurity)
Since these technologies have been in use for many years, it is critical to make security a part of the package.
Implementation considerations when choosing a protocol
Privacy is an essential requirement for implementation. Almost all systems require secure communication with the cloud to ensure that personal data cannot be accessed or modified. In addition, the management of devices and data displayed in the cloud needs to be managed separately. Without this feature, the user's key personal information cannot be properly protected and is available to anyone with administrative privileges.
Management platforms generally also include:
system initialization
Remote field service options (such as field upgrades, reset to default parameters, and remote tests)
Control account usage (such as account disabling, account activation, and billing features)
Control for theft purpose (equivalent to breaking the device)
Considering this type of architecture, there are some additional protocols and procedures to consider:
Custom developed cloud system management application
Snmp managed sensor node collection
Cloud computing integration programRun SQLite to store and selectively update data to the cloud
Billing is an important aspect of business systems. Telecom operators have proven that the monthly subscription model is the best revenue option. In addition, the choice and integration of automated services is also important for seamless billing. In addition, credit card dependencies can also cause problems, including over quota issues, expired credit cards, and deleted accounts.
User self-service is also the key to success. This includes remote field service so that the device does not return to the factory, intelligent or automated configuration, online help, community assistance and very intuitive products are key.
Application integration is also important. Today, point systems dominate, but the key to the future will be to make sensors available for a wide range of applications. Accuracy and reliability can have a significant impact on the results of the results application, and once a standard interface emerges, it is expected to compete in this area. Indirect access through the server ensures security, evolution without application changes, and billing control.
Discontinuous operations and big data are closely linked. As the device is randomly connected and disconnected, you need to save the data for the sensor and update the cloud at a later time. Storage restrictions exist for power and cost reasons. If some data is critical, it can be saved when other data is discarded. All data can be saved and optionally updated later in the cloud. The algorithm that processes the data can run on a cloud or sensor or any intermediate node. All of these options present special challenges for sensors, clouds, communications, and external applications.
Multi-connected sensor access is also a requirement to make sensors truly available for a wide range of applications. This type of connection is most likely to be done through the server to simplify the sensor and eliminate the power requirements of duplicate messages.
In summary, many protocols have been touted as the ideal solution for the Internet of Things (IoT). Often the right protocol choices are overshadowed by suppliers who have a vested interest in their products. Users must understand their specific requirements and limitations and have an accurate system specification to ensure that the right protocols are selected for the various management, application, and communication functions, and that all implementation specifications are met.
15W Wall-Mounted Power Adapter
15W Wall-Mounted Power Adapter,24V0.5A Ac Dc Power Adapter,5V2A Power Adapter,5V2.5A Clear Enclousure Wall Charger
Guangdong Mingxin Power Technologies Co.,Ltd. , https://www.mxpowersupply.com