If only judged from "free" or "open", the RISC-V architecture is not the first processor architecture to be free or open.
Before we get started, let's analyze the differences between the RISC-V architecture and why other open architectures have not achieved enough success by discussing several representative open architectures.
0.1 Civilian Heroes - OpenRISCOpenRISC is an open source RISC processor based on the GPL protocol provided by the OpenCores organization.
OpenRISC has the following features:
A free 32/64-bit RISC architecture is available.
The processor source code based on the architecture is implemented in Verilog HDL (Hardware Description Language).
Has a complete tool chain.
OpenRISC is applied to projects in many companies. It can be said that OpenRISC is an open source processor implementation that is widely used.
The shortcoming of OpenRISC is that it focuses on implementing an open source CPU Core, rather than defining an open instruction set architecture, so its architecture is not fully developed, and the definition of the instruction set is not mentioned in the previous section. The advantages of the RISC-V architecture have not risen to the height of the establishment of a dedicated foundation organization. OpenRISC is more often considered an open source Core than a beautiful instruction set architecture. In addition, OpenRISC's license is GPL, which means that all instruction set changes must be open source (and RISC-V does not have this constraint).
0.2 giants expensive - SPARCSPARC Architecture As one of the classic RISC microprocessor architectures, SPARC was first designed by Sun Computer in 1985. SPARC is also a registered trademark of SPARC International, Inc., which was established in 1989 to promote the SPARC architecture and conduct compatibility testing for the architecture. In order to promote the SPARC ecosystem, SPARC International has opened the standard and licensed it to a number of manufacturers, including Texas Instruments, Cypress Semiconductor and Fujitsu. Since the SPARC architecture is also completely open to the outside world, a fully open source LEON processor has also emerged. Not only that, but in 1994, Sun also promoted the SPARC v8 architecture to become the IEEE standard (IEEE Standard 1754-1994).
Since the original intention of the SPARC architecture is designed for the server domain, its biggest feature is that it has a large register window. The SPARC-compliant processor needs to implement from 72 to 640 general-purpose registers, each with a width of 64 bits. Form a series of register sets, called register windows.
The architecture of this register window, because it can switch between different register sets to quickly respond to function calls and returns, can produce very high performance, but this architecture is too expensive for power consumption area, and is not suitable for PC and Embedded domain processor. The SPARC architecture is also not modular, making it impossible for users to tailor and select. It is difficult to replace the commercial x86 and ARM architectures as a general-purpose processor architecture.
Designing such a large server CPU chip is not something that ordinary companies and individuals can get involved in, and companies that have the ability to design such a large CPU do not have to invest huge costs to challenge the dominance of x86. With the weakness of Sun, the SPARC architecture is now largely out of sight. Interested readers please search for the article "Goodbye SPARC Processor, Goodbye Sun" on the Internet.
0.3 prestigious students - RISC-VThe RISC-V experience at the birth of Berkeley University is not repeated here.
Because many free or open architectures have appeared in the CPU field for many years, many universities have also introduced a variety of instruction set architectures in research projects. Therefore, when I first heard about RISC-V, I thought it was a toy, or a purely academic research project.
Until the author personally read through the RISC-V architecture document, can not help but be impressed by its advanced design philosophy. At the same time, the various advantages of the RISC-V architecture have also been favored by many professionals and many commercial companies have joined. And the official launch of the 2016 RISC-V Foundation has had a significant impact in the industry. As such, RISC-V is the most revolutionary open processor architecture to date.
1 Simple is beautiful - the design philosophy of RISC-V architectureThe RISC-V architecture is an instruction set architecture. Before we introduce the details, let us first understand the philosophy of design. The so-called "philosophy" of design is a strategy advocated by it. For example, the design philosophy of the Japanese car we know well is economical and fuel-efficient, and the design philosophy of American cars is domineering. What is the design philosophy of the RISC-V architecture? It is "avenue to Jane".
One of the most admired design principles of the author is that simplicity is beauty, and simplicity means reliability. Numerous practical cases have proved the truth of “simple means reliableâ€, and the more complicated the machine, the more error-prone it is.
The so-called avenue to Jane, in the actual work of IC design, I have seen the most succinct design to achieve safe and reliable, and have seen the most complicated design for a long time can not be stable convergence. The most succinct design is often the most reliable and is tested again and again in most project practices.
The work of IC design is very special. The final output is chip. The design and manufacturing cycle of a chip is very long. It can't be upgraded and patched as easily as software code. Every time the chip is revised to delivery. A few months of the cycle. Not only that, the cost of a chip's manufacturing is high, ranging from hundreds of thousands of dollars to hundreds of millions of dollars. These characteristics all determine the cost of trial and error for IC design is extremely high, so it is very important to effectively reduce the occurrence of errors.
The scale of modern chip design is getting bigger and bigger, and the complexity is getting higher. It does not mean that designers are required to evade the use of complicated technology. Instead, they should use good steel on the cutting edge and use the most complicated design in the most. The key scenarios, in most cases of choice, try to choose a simple implementation.
When I read the RISC-V architecture document for the first time, I couldn't help but praise the film and surprise it. Because the RISC-V architecture constantly emphasizes in its documentation, its design philosophy is “avenue to simplicity†and tries to pass the architecture. The definition makes the implementation of the hardware simple enough. Its simplicity is the philosophy of beauty, which can be easily seen from several aspects, and the subsequent sections will be discussed one by one.
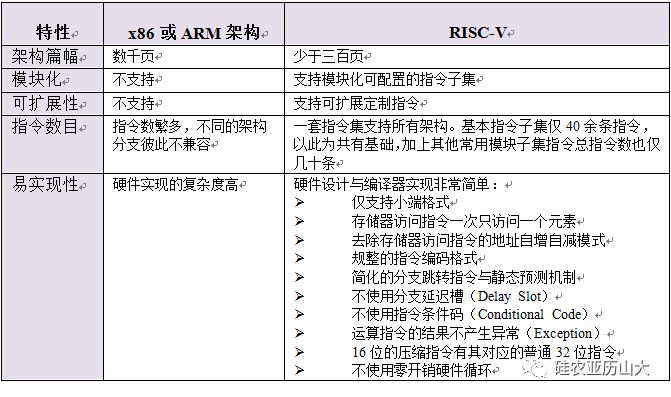
1.1 No disease, light body - the length of the architectureIn the field of processors, the current mainstream architecture is x86 and ARM architecture. I have been involved in the design of ARM architecture application processors, so I need to read the ARM architecture documentation, if the readers familiar with it should understand its length. After decades of development, the architecture of modern x86 and ARM architectures has reached hundreds of thousands of pages. It can be printed with half a table high, but it is really a "work".
The reason why modern x86 and ARM architecture documents are thousands of pages and there are many versions, one of the main reasons is that the development of its architecture is accompanied by the continuous development of modern processor architecture technology.
And as a commercial architecture, in order to be able to maintain the backward compatibility of the architecture, it has to retain a lot of outdated definitions, or in the definition of the new architecture part in order to be able to put the existing technical part is very awkward. Over time, it becomes extremely lengthy.
So whether the modern mature architecture can choose to start over and redefine a simple architecture can be said to be almost impossible. One of the important reasons is that it is not forward compatible and cannot be accepted by users. Imagine if we bought a new computer or mobile phone with a new processor to go home, all the previous software can not run and become brick, it is certainly unacceptable.
The RISC-V architecture, which is now available, has the advantage of latecomer. Since the computer architecture has become a mature technology after years of development, the problems exposed in the process of continuous maturity have been thoroughly studied. The new RISC-V architecture can be circumvented and has no historical burden of backward compatibility, which can be said to be disease-free.
The current "RISC-V Architecture Document" is divided into "Instruction Set Document" (riscv-spec-v2.2.pdf) and "Privilege Architecture Document" (riscv-privileged-v1.10.pdf). The "Instruction Set Document" is 145 pages long, while the "Privilege Architecture Document" is only 91 pages long. Engineers who are familiar with the architecture can read through it in one to two days. Although the "RISC-V architecture documentation" is constantly enriched, compared to "x86 architecture documentation" and "ARM architecture documentation", RISC- The length of V can be said to be extremely short and fine.
Interested readers can download their documentation for free on the RISC-V Foundation's website (https://riscv.org/specifications/) without registration, as shown in Figure 1.
Figure 1 Architecture document on the RISC-V Foundation website
1.2 Ability to flex - modular instruction setThe biggest difference between the RISC-V architecture and other mature commercial architectures is that it is a modular architecture. As a result, the RISC-V architecture is not only short and succinct, but its different parts can be organized in a modular way, trying to satisfy a variety of different applications through a unified architecture.
This modularity is not available in x86 and ARM architectures. Taking ARM architecture as an example, ARM architecture is divided into three series: A, R and M, which are respectively targeted at Application (application operating system), Real-Time (real-time) and Embedded (embedded). Not compatible.
However, the modular RISC-V architecture enables users to flexibly choose different combinations of modules to meet different application scenarios. It can be said to be “all agesâ€. For example, for small-area low-power embedded scenarios, users can select the RV32IC combination instruction set, only using Machine Mode; while high-performance application operating system scenarios can choose the instruction set such as RV32IMFDC, using Machine Mode ( Machine mode) and User Mode (user mode) two modes. And their common parts are compatible with each other.
1.3 Concentrate is the essence - the number of instructionsThe short architecture and modular philosophy make the number of instructions in the RISC-V architecture very simple. The basic number of RISC-V instructions is only 40, plus a total of dozens of other modular extension instructions.
2 Introduction to RISC-V Instruction Set ArchitectureThis chapter provides a brief introduction to the various features of the RISC-V instruction set architecture.
2.1 modular instruction subsetThe RISC-V instruction set is organized in a modular way, with each module being represented by an English letter. The most basic and only mandatory implementation of RISC-V is the subset of basic integer instructions represented by the I letter. With this subset of integer instructions, a complete software compiler can be implemented. The other instruction subsets are optional modules, and the representative modules include M/A/F/D/C, as shown in Table 1.
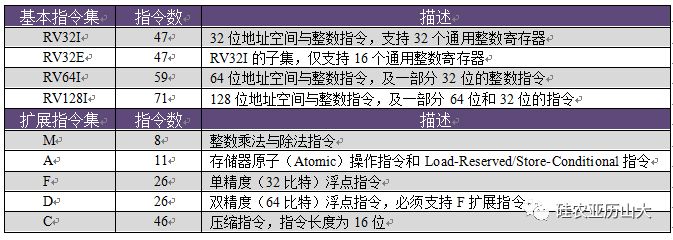
Table 1 Modular Instruction Set for RISC-V
To increase code density, the RISC-V architecture also provides an optional subset of "compressed" instructions, represented by the English letter C. The instruction code length of the compression instruction is 16 bits, and the length of the ordinary non-compression instruction is 32 bits. A specific combination of these modules, "IMAFD", also referred to as the "universal" combination, is represented by the English letter G. Therefore, RV32G represents RV32IMAFD, and similarly RV64G represents RV64IMAFD.
To further reduce the area, the RISC-V architecture also provides an "embedded" architecture, represented by the English letter E. This architecture is primarily used in deep embedded scenarios where very low area and power consumption are pursued. The architecture only needs to support 16 general-purpose integer registers, while the non-embedded common architecture needs to support 32 general-purpose integer registers.
Through the above modular instruction set, different combinations can be selected to meet different applications. For example, an embedded scene with a small area and low power consumption can choose to use the RV32EC architecture; for a large 64-bit architecture, the RV64G can be selected.
In addition to the above modules, there are several modules including L, B, P, V, and T. Most of these extensions are still being refined and defined, and have not yet been finalized, so this article will not discuss them in detail here.
2.2 configurable general purpose register setThe RISC-V architecture supports a 32-bit or 64-bit architecture. The 32-bit architecture is represented by RV32. Each general-purpose register has a width of 32 bits. The 64-bit architecture is represented by RV64, and each general-purpose register has a width of 64 bits.
RISC-V architecture integer general register set, containing 32 (I architecture) or 16 (E architecture) general integer registers, where integer register 0 is reserved as constant 0, the other 31 (I architecture) or 15 (E-Architecture) is a general-purpose general-purpose integer register.
If a floating point module (F or D) is used, then another separate floating point register set is required, containing 32 general purpose floating point registers. If only the F-module floating-point instruction subset is used, each general-purpose floating-point register has a width of 32 bits; if a D-module floating-point instruction subset is used, each general-purpose floating-point register has a width of 64 bits.
2.3 Regular instruction codeReading the general register bank as soon as possible in the pipeline is often one of the expectations of processor pipeline design, which can improve processor performance and optimize timing. This seemingly simple principle is difficult to implement in many existing commercial RISC architectures, because after many years of repeated modifications and new instructions are added, the register index position in the instruction code becomes very messy, which puts a burden on the decoder. .
Thanks to the advantages of the latecomer and the lessons learned from the development of the processor over the years, the instruction set encoding of RISC-V is very regular, and the index of the general-purpose register required by the instruction is placed in a fixed position, as shown in Figure 2. Shown. Therefore, the Instruction Decoder can easily decode the register index and then read the Register File (Regfile).
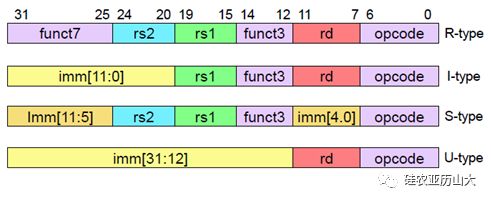
Figure 2 RV32I regular instruction encoding format
2.4 Simple memory access instructionsLike all RISC processor architectures, the RISC-V architecture uses dedicated memory read and store instructions to access memory. Other common instructions cannot access the memory. This architecture is RISC architecture. A common basic strategy that makes the hardware design of a processor core simple.
The basic unit of memory access is Byte. RISC-V's memory read and memory write instructions support one byte (8-bit), half-word (16-bit), single-word (32-bit) memory read and write operations, and support for a double word in 64-bit architecture. (64-bit) memory read and write operations.
The memory access instructions of the RISC-V architecture also have the following salient features:
In order to improve the performance of memory read and write, RISC-V architecture recommends the use of address-aligned memory read and write operations, but the address unaligned memory operation RISC-V architecture also supports, the processor can choose to use hardware to support, you can also choose software To support.
Since the current mainstream application is Little-Endian, the RISC-V architecture only supports the little endian format. For the definition and difference between the little endian format and the big endian format, this article does not introduce too much here. If you don't know this well, beginners can refer to it.
Many RISC processors support address auto-increment or self-decrement mode. This self-increasing or self-decreasing mode can improve the performance of the processor accessing the contiguous memory address range, but it also increases the difficulty of designing the processor. The memory read and memory write instructions of the RISC-V architecture do not support the mode of address increment and decrement.
The RISC-V architecture uses the Relaxed Memory Model, which does not require the order of execution of memory read and write instructions to access different addresses, unless explicitly addressed using explicit memory barrier (Fence) instructions.
These choices clearly reflect the philosophy of the RISC-V architecture that simplifies the basic instruction set and simplifies hardware design. The RISC-V architecture is so well defined that it can achieve the effect of flexing. For example, for a simple CPU with low power consumption, a very simple hardware circuit can be used to complete the design; for a high-performance superscalar processor, the performance can be improved by the dynamic hardware scheduling capability of the complex design.
2.5 Efficient branch jump instructionsThe RISC-V architecture has two Unconditional Jumps, jal and jalr instructions. The Jump and Link instruction jal can be used to make a subroutine call, and the subroutine return address is stored in the link register (Link Register: held by a general integer register). The jump and link-register instruction jalr instruction can be used for the subroutine return instruction. By using the link register saved by the jal instruction (jump into the subroutine) for the base address register of the jalr instruction, the subroutine can be used. The program returns.
The RISC-V architecture has six conditional branch instructions. This conditional jump instruction uses two integer operands as well as ordinary arithmetic instructions, and then compares them. If the comparison conditions are met. Then, jump. Therefore, such instructions will be compared to the jump two operations placed in an instruction.
For comparison, many other RISC architecture processors require two separate instructions. The first instruction first uses the comparison instruction, and the comparison result is saved to the status register. The second instruction uses the jump instruction to determine that the previous instruction is stored in the status register and the comparison result is true. In contrast, this conditional jump instruction of RISC-V not only reduces the number of instructions, but also makes the hardware design simpler.
For low-end CPUs without a hardware branch predictor, the RISC-V architecture explicitly requires a default static branch prediction mechanism to ensure its performance, ie if it is a conditional jump instruction that jumps backwards, the prediction is "jump"; if it is a conditional jump instruction that jumps forward, it is predicted to be "no jump", and the RISC-V architecture requires the compiler to compile and generate assembly code according to this default static branch prediction mechanism, thus allowing The low-end CPU can also get good performance.
In order to make the hardware design as simple as possible, the RISC-V architecture specifically defines that all offsets with a conditional jump instruction jump target (relative to the current instruction's address) are signed numbers, and their sign bits are encoded in a fixed number. s position. Therefore, this static prediction mechanism is very easy to implement on hardware. The hardware decoder can easily find this fixed position and judge whether it is 0 or 1 to judge whether it is positive or negative. If it is negative, it means jump. The destination address is the current address minus the offset, that is, the backward jump, and the prediction is "jump". Of course, for high-end CPUs equipped with hardware branch predictors, advanced dynamic branch prediction mechanisms can be used to ensure performance.
2.6 Concise subroutine callIn order to understand this section, we need to introduce the process of calling sub-functions in the general RISC architecture. The process is as follows:
After entering the sub-function, a memory write (Store) instruction is needed to save the current context (the value of the general-purpose register, etc.) to the stack area of ​​the system memory. This process is usually called "save scene".
At the time of exiting the subroutine, a memory read (Load) instruction is required to read the previously saved context (the value of the general purpose register, etc.) from the stack area of ​​the system memory, a process commonly referred to as "recovery site."
The process of "save the scene" and "restore the scene" is usually done by instructions compiled by the compiler, and developers who develop in high-level languages ​​(such as C or C++) don't have to care too much about this. A high-level language program can directly write a sub-function call, but the process of "save scene" and "restore scene" that occurs at the bottom is actually happening (can be seen from the compiled assembly language) Those "save scenes" and "restore scenes" assembly instructions), and also need to consume a lot of CPU execution time.
In order to speed up the process of "storing the scene" and "restoring the scene", some RISC architectures have invented a program that writes multiple registers to a single store (Store Multiple) at a time, or reads multiple registers at a time (Load Multiple) from memory. The advantage of such an instruction is that a single instruction can accomplish a lot of things, thereby reducing the amount of code of the assembly instruction and saving the space of the code. However, the drawbacks of such "Load Multiple" and "Store Multiple" are that the CPU hardware design is complicated, the hardware overhead is increased, and the timing can be damaged, so that the CPU frequency cannot be improved. I have designed such a processor. I was deeply affected by it.
The RISC-V architecture abandoned the use of such "Load Multiple" and "Store Multiple" instructions. And explain that if there are occasions that prefer the number of instructions for "save the scene" and "restore the scene", then you can use a common library (specially used to save and restore the scene), so you can save Each number of sub-function calls is placed with a number of "Save Site" and "Restore Site" instructions.
This choice once again confirms RISC-V's philosophy of pursuing hardware simplicity, because abandoning the "Load Multiple" and "Store Multiple" instructions can greatly simplify the hardware design of the CPU. For low-power, small-area CPUs, you can choose very simple circuits to implement. The high-performance superscalar processor has strong dynamic scheduling capability, and can have powerful branch prediction circuits to ensure that the CPU can quickly jump execution, so that you can choose to use a common library (specially used to save and restore the scene). The way to reduce the amount of code, but at the same time achieve high performance.
2.7 Unconditional Code ExecutionMany early RISC architectures invented instructions with conditional codes. For example, the first few bits of the instruction code represent a Conditional Code, and the instruction is actually executed only if the condition corresponding to the condition code is true.
This form of encoding the condition code into the instruction allows the compiler to compile a short loop into a conditional code instruction without compiling into a branch jump instruction. This reduces the occurrence of branch jumps, on the one hand reduces the number of instructions; on the other hand, it avoids the performance loss caused by branch jumps. However, the drawbacks of this "condition code" instruction will also complicate the hardware design of the CPU, increase the overhead of the hardware, and may damage the timing so that the CPU's main frequency cannot be improved. I have been deep in designing such a processor. Suffer from it.
The RISC-V architecture abandons the use of this "conditional code" instruction, using ordinary conditional branch jump instructions for any conditional judgment. This choice once again confirms RISC-V's philosophy of pursuing hardware simplicity, because abandoning the "conditional code" instruction can greatly simplify the hardware design of the CPU, and for a low-power small-area CPU, a very simple circuit can be selected for implementation. The high-performance superscalar processor has strong dynamic scheduling capability, and can have powerful branch prediction circuits to ensure that the CPU can quickly jump execution to achieve high performance.
2.8 no branch delay slotMany of the early RISC architectures used the "Delay Slot". The most representative one is the MIPS architecture. In many classic computer architecture textbooks, MIPS is used to introduce the branch delay slot. The branch delay slot means that one or several instructions following each branch instruction are not affected by the branch jump. The next few instructions will be executed regardless of whether the branch jumps.
The reason why many of the early RISC architectures adopted the branch delay slot was mainly because the processor pipeline at that time was relatively simple and did not use the advanced hardware dynamic branch predictor, so the use of the branch delay slot can achieve considerable performance effects. However, this kind of branch delay slot makes the hardware design of the CPU extremely awkward, and CPU designers are often miserable.
The RISC-V architecture abandons the branch delay slot and reaffirms the philosophy of RISC-V to simplify hardware, because the branch prediction algorithm of modern high-performance processors is very accurate, and powerful branch prediction circuits can ensure accurate CPU. The predicted jump execution achieves high performance. For low-power, small-area CPUs, the hardware is greatly simplified because it does not need to support branch delay slots, which further reduces power consumption and improves timing.
2.9 Zero-free overhead hardware loopMany RISC architectures also support Zero Overhead Hardware Loop instructions, which are thought of by the direct involvement of the hardware, by setting some Loop Count registers, and then allowing the program to automatically loop through each loop. The Loop Count is automatically decremented by 1, so that the loop continues until the value of the Loop Count becomes 0, exiting the loop.
The reason for inventing this hardware-assisted zero-overhead loop is because of the for loop in software code (for i=0; i However, there must be some loss, such zero-overhead hardware loop instructions greatly increase the complexity of hardware design. Therefore, the zero-overhead loop instruction is exactly the opposite of the philosophy of the RISC-V architecture to simplify hardware. Naturally, such zero-overhead hardware loop instructions are not used in the RISC-V architecture. It is mentioned in Section 2.1 of this chapter that the RISC-V architecture uses a modular approach to organizing different subsets of instructions. The most basic integer instruction subset (I letter representation) supports operations such as addition, subtraction, shift, and bitwise. Logical operations and comparison operations. These basic operations can perform more complex operations (such as multiplication and division and floating-point operations) by combining or functioning libraries, thus enabling most software operations. The operations supported by the integer multiplication and division instruction subset (M letter representation) include signed or unsigned multiplication and division operations. The multiplication operation can support the multiplication of two 32-bit integers to obtain a 64-bit result; the division operation can support the division of two 32-bit integers to obtain a 32-bit quotient and a 32-bit remainder. The operations supported by the single-precision floating-point instruction subset (F-letter representation) and the double-precision floating-point instruction subset (D-letter representation) include floating-point addition and subtraction, multiplication and division, multiply and accumulate, square root and comparison operations, and Integer and floating point, single-precision and double-precision floating-point format conversion operations between each other. Many RISC-based processors generate software exceptions when the operation instruction generates an error, such as Overflow, Underflow, Subnormal, and Divide by Zero. A special feature of the RISC-V architecture is that it does not generate an exception for any of the arithmetic instruction errors (including integer and floating point instructions), but instead generates a special default value and sets the status bits of some status registers. The RISC-V architecture recommends software to find these errors in other ways. Again, it clearly reflects the philosophy of the RISC-V architecture that simplifies the basic instruction set to simplify the hardware design. The basic RISC-V basic integer instruction subset (indicated by the letter I) specifies an instruction length of 32 bits of equal length. This isometric instruction definition makes it very easy to design a basic RISC-V CPU that only supports a subset of integer instructions. However, an equal length 32-bit encoding instruction can also cause a relatively large code size. In order to satisfy certain scenarios where the code size is high (such as the embedded field), RISC-V defines an optional subset of Compressed instructions, represented by the letter C, or by RVC. RISC-V has the advantage of latecomer. From the beginning, it has planned the compression instruction, and reserved enough coding space. The 16-bit long instruction and the ordinary 32-bit long instruction can be seamlessly and freely intertwined, and the processor is not defined. Extra status. Another special feature of the RISC-V compression instruction is that the compression strategy of the 16-bit instruction is to compress and rearrange the information in some common and most commonly used 32-bit instructions (for example, suppose an instruction uses two identical operations. The number index can save the coding space of one of the indexes, so each 16-bit instruction can find its corresponding original 32-bit instruction one by one. Therefore, compiling the program into a compressed instruction can only be done in the assembler stage, greatly simplifying the burden on the compiler tool chain. The RISC-V architecture researchers conducted detailed code volume analysis, as shown in Figure 3. As can be seen from the analysis results, the RV32C code size is reduced by 40% compared to the RV32 code size, and with ARM, MIPS has a good performance compared to architectures such as x86.
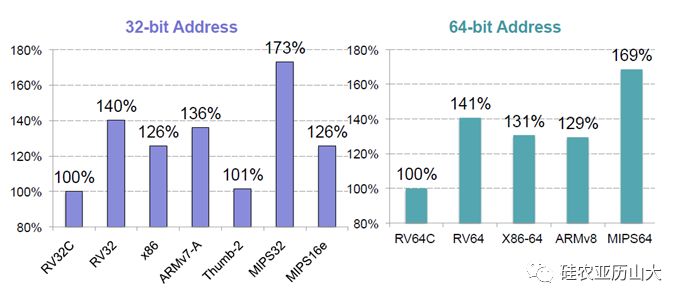
Figure 3 Code density comparison of each instruction set architecture (the smaller the data, the better)
2.12 privileged modeThe RISC-V architecture defines three modes of operation, also known as Privileged Mode:
Machine Mode: Machine mode, referred to as M Mode.
Supervisor Mode: Supervised mode, referred to as S Mode.
User Mode: User mode, referred to as U Mode.
The RISC-V architecture defines M Mode as a mandatory mode and the other two are optional. Different systems can be implemented through different combinations of modes.
The RISC-V architecture also supports several different memory address management mechanisms, including management mechanisms for physical addresses and virtual addresses, enabling the RISC-V architecture to support everything from simple embedded systems (directly operating physical addresses) to complex operating systems. Various systems (directly operating virtual addresses).
2.13 CSR RegisterThe RISC-V architecture defines a number of Control and Status Registers (CSRs) that are used to configure or log the status of some operations. The CSR register is a register internal to the processor core, and its own address encoding space is completely independent of the address range addressed by the memory.
Access to the CSR register uses dedicated CSR instructions, including CSRRW, CSRRS, CSRRC, CSRRWI, CSRRSI, and CSRRCI instructions.
2.14 Interrupts and exceptionsInterrupt and exception mechanisms are often the most complex and critical part of the processor instruction set architecture. The RISC-V architecture defines a relatively simple set of interrupt and exception mechanisms, but also allows users to customize and extend them.
2.15 Vector Instruction SubsetAlthough the RISC-V architecture does not currently have a subset of the vector vector, it can be seen from the current draft that the design concept of the RISC-V vector instruction subset is very advanced, due to the latecomer advantage and the vector architecture. With years of maturity, the RISC-V architecture will use variable-length vectors instead of vector-length SIMD instruction sets (such as ARM's NEON and Intel's MMX) to flexibly support different implementations. CPUs that pursue low-power, small-area CPUs can choose to implement hardware vectors with shorter lengths, while high-performance CPUs can choose longer hardware vectors for implementation, and the same software code can be compatible with each other.
2.16 Custom Instruction ExtensionIn addition to the extensibility and choice of the modular instruction subset described above, a very important feature of the RISC-V architecture is the support for third-party extensions. Users can extend their own subset of instructions. RISC-V reserves a large amount of instruction encoding space for user-defined extensions. At the same time, four Custom instructions are defined for users to use directly. Each Custom instruction has several The sub-encoding space of the bit is reserved, so the user can directly extend dozens of custom instructions using four Custom instructions.
2.17 Summary and comparisonAfter decades of processor design technology, with the development of large-scale integrated circuit design technology until today, the following characteristics are presented:
Since the hardware scheduling capability of high-performance processors is already very strong and the frequency is very high, the hardware design hopes that the instruction set is as regular and simple as possible, so that the processor can design a higher main frequency and a lower area. .
Very low power processors based on IoT applications are more demanding for low power and low area.
Memory resources are also more abundant than earlier RISC processors.
As a result of these factors, many of the early RISC architecture design concepts (born according to the technical background at the time) have not only failed to help modern processor design, but have become a burden. Some of the features defined in the early RISC architectures, on the one hand, make the hardware design of high-performance processors sway; on the other hand, the extremely low-power processor hardware design bears unnecessary complexity.
Thanks to the latecomer advantage, the new RISC-V architecture can circumvent all of these known burdens while designing a “modern†instruction set using its advanced design philosophy. This section summarizes its characteristics again as shown in Table 2.
Table 2 Summary of RISC-V instruction set architecture features
The mechanical Buzzer uses a magnet to move a reed up and down quickly to emit a lower-pitch buzz! It's quieter than the piezoelectric buzzer but uses more power, so you the terminals will have to be closer to the battery packs. To use them, you'll need to match the wire colors to the wires from the battery pack.
Piezo Beeper,Mechanical Buzzer,Piezo Mechanical Buzzer,Low Frequency Mechanical Buzzer
Jiangsu Huawha Electronices Co.,Ltd , https://www.hnbuzzer.com