The ARM11 (S3C6410) processor is selected as the hardware platform, and the embedded Linux operating system is used as the software platform. The background difference method and the interframe difference method for moving image detection are combined with the GSM module to design and implement an application. An unattended moving target detection system in a home environment or private office. The overall scheme of system design was put forward, and the design flow of the system software and hardware platform was introduced in detail. Finally, the system was tested.
With the development of society and the advancement of science and technology, people's security awareness is getting stronger and stronger, and computer network technology, communication technology, and digital video coding technology are becoming more and more mature, making computer-based multimedia video surveillance systems possible. However, the traditional video surveillance system is very complicated, power consumption and cost are high and need to be on duty, but can not be applied to places such as home or private office. For this reason, this paper designs an ARM11 core processor, embedded Linux. For the operating system, the target detection algorithm is added on the basis of the traditional video surveillance, and combined with the GSM module, has reached the goal of unattended.
1 overall system designThe moving target detection system adopts S/B (server/browser) working mode, and is generally divided into a server monitoring module, a short message notification module (GSM) and a customer viewing module. The server monitoring module uses Samsung's ARM11 (S3C6410) microprocessor, open source Linux operating system, and GSM module uses Q2403A chip. When the monitored picture changes, that is, when the moving target is detected, the server will change the image to the picture. The format is stored and sent to the client. At the same time, the 2403A will notify the client by SMS, and the client can view the result of the image change through the IE browser. The overall design of the system is shown in Figure 1.
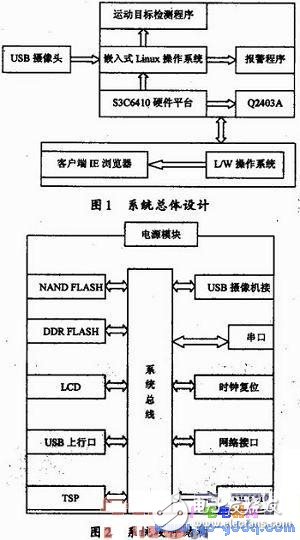
This article uses TIny6410 development board of Guangzhou Friendly Arm Company. TIny6410 is an embedded board with ARM11 (Samsung S3C6410) as the main processor. The CPU is based on ARM11-76JZF-S core design and integrates powerful multimedia unit. . The hardware architecture is shown in Figure 2. The SMS notification module Q2403A is a GSM GPRS module introduced by WAVECOM. It is small in size and light in weight. It is mainly composed of RF antenna, internal FLASH, SRAM and GSM baseband processor, matching power supply and a 40-pin ZIF socket. . The GSM baseband processor is the core component, and its function is equivalent to a coprocessor, which is used to process the AT commands sent by the external system through the serial port.
3 software platform The system software platform is based on the Linux operating system. First, establish a cross-compilation environment on the host machine and install the cross-compiler arm-Linux-gCC. Secondly, the U-Boot and Linux 2.6.33 kernels are ported and compiled, and the root file system based on busy-box 1.13.3 is built. Due to the limitations of embedded server resources, including memory size, CPU processing power, etc. . Therefore, in the design process, the kernel needs to be tailored to improve the system performance while reducing the system resource occupation. The motion detection application and the SMS alarm program are written on the tailored Linux operating system.
3.1 Moving target detection algorithm under embedded Linux At present, there are two main research directions for detecting moving objects and measuring motion parameters, namely: using artificial neural networks and using image processing methods, most experts and scholars have The research focuses on the use of image processing methods for moving target detection and tracking. The more effective methods for image moving target detection are mainly optical flow method and differential image method. Generally speaking, the time overhead of optical streaming is large, and its real-time and practicality. On the contrary, the image difference method is relatively simple and easy to implement. The image difference method can be divided into two categories: background image difference method and interframe difference method. The background image difference method is a subtraction operation between the current frame and the background image of the most direct and simple sequence image in the conventional moving object detection method. Since there is a difference in gray scale or color between the moving object and the background, the value of each pixel in the subtracted result is compared with a preset threshold, and if the value of the pixel is greater than the set threshold, the determination is There are moving objects in the monitored scene, and the target of the motion is always obtained. The principle of background image difference method is simple, but it is also affected by changes in external conditions such as light and weather. The interframe difference method is a method for obtaining a moving target contour by performing differential operations on two adjacent frames in a video image sequence. It can be well applied to the case where there are multiple moving targets and camera movements. When an abnormal object motion occurs, there will be a significant difference between the frame and the frame. The two frames are subtracted, and the absolute value of the brightness of the two frames is obtained. It is judged whether it is greater than the threshold to analyze the motion characteristics of the video or image sequence, and the image sequence is determined. Whether there is object motion in or not, the image sequence is frame-by-frame difference, which is equivalent to high-pass filtering in the time domain of the image sequence. The interframe difference method is not sensitive to scene changes such as light, and can adapt to various dynamic environments with good stability. The disadvantage is that the complete region of the object cannot be extracted, and only the boundary can be extracted. When almost completely overlapping, no moving objects are detected. In view of the advantages and disadvantages of the background difference method and the interframe difference method, the two methods are combined to complement each other. In the video image sequence, using the existing background difference method and the inter-frame difference method as the revelation, the continuous two-frame difference image and the background difference image in the moving image are directly operated and operated, and the result is binarized to obtain the motion result. .
3.2 Algorithm Description The algorithm description is as follows:
(1) Perform 3x3 median filtering preprocessing on the sequence image to remove the random noise of the image. Reduce the complexity of subsequent operations and overcome the interference of noise on image processing results;
(2) selecting a background image Bk(x, y) from the sequence of video images to include only a fixed background image;
(3) selecting two consecutive frames of images in the video image sequence, wherein the previous frame image Pk-1(x, y);
(4) Calculate the difference between the current frame and the background frame by FD(x, y), and extract the complete target from the image;
(5) Calculating the difference between the current frame and the previous frame by FD(x, y), and obtaining the amount of change of the target;
(6) Find the intersection of the frame difference FD(x, y) and FG(x, y) to obtain a motion region image with a rough moving target;
(7) Mathematical morphology operation makes the motion area closed, continuous and complete, and removes noise in the background.
among them:
Where T is the threshold. For an image of a given video sequence, assuming that there is no motion at pixel k, the frame difference also obeys the Gauss distribution N(O, σ2) with a mean of 0 and a variance of σ2:
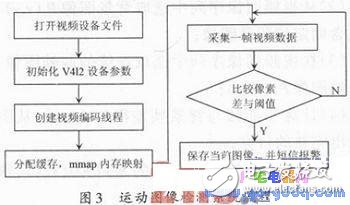
Where: H0 represents no motion hypothesis; σ2 is the statistical variance of the frame difference, which is generally considered to be equal to twice the variance of the camera noise. The "3σ" rule is tested according to the probability statistical hypothesis and according to the principle that "the correct threshold T should be able to eliminate most of the noise". The threshold T tested by the experiment can be selected between 5 and 15 in the context of the application of the system. Based on the above algorithm, the specific implementation of the system is shown in Figure 3.
3.3 GSM module SMS notification For the GSM module, all operations are through the AT command (the AT command is the terminal or computer connected to the MODEM to start with "AT" (except for two immediate execution commands) Enter a set of commands to complete the implementation. When programming, the AT command is first sent as data to the GSM module through the data serial port. The GSM module interprets the received data as an AL command, and then performs a response operation according to the command. The specific operation is as follows: the header file required for serial port operation, open the serial port, the serial port related file under linux is located under /dev, and the serial port is opened by using the standard file open function operation: fd=open("/dev/ttySO", O_RDWR); Set the most basic settings of the serial port. The serial port includes the baud rate, parity bit and stop bit settings. The setting of the serial port is mainly to set the member values ​​of the struct termios structure; set the short message sending format (O_PDU, 1_text); send a short message. For example, if the content of the short message is hel lo, the AT command should be AT+CMGS=“139# # # # #2312â€>hello^z (^z means CTRl+z); close the serial port close(fd).
3.4 Image Transmission There are many ways to implement streaming media network transmission. HyperText Transfer Protocol (HTTP) is a transmission protocol for transmitting hypertext from a WWW server to a local browser. It belongs to the client browser and The application communication layer protocol between web servers, which can make the browser more efficient and reduce network transmission. The HTTP protocol adopts the request/response mode. The specific implementation process is: embedding the embedded web server in the embedded development board S3C6410. After completing the configuration, the user first enters the URL address in the address bar, and the client browses at this time. The device opens a Socket file, indicating that the connection is successfully established, and the request is submitted to the Web server through the Socket client browser IE. The Web server processes the request after receiving the request, and sends the result back to the client browser IE via HTTP. After the browser IE establishes a connection with the server, the system ("tar") and system ("cp") are used to package and copy the pictures stored on the development board to the main directory of the web server, and write the main directory. Hypertext Marked Language (HTML) is a simple markup language used to create hypertext documents. The Hypertext Transfer Protocol specifies the rules and operations that the browser follows when running HTML documents. The most extreme browser in the HTML file can access images saved in the server's home directory. The specific format is: hyperlink name, the label indicates the beginning of a link, indicating the end of the link.
The whole system is tested in a simulated environment, and the system is started. After the system is stable, an object in the field of view of the camera is moved to change the screen of the monitoring. At this time, the system will send a text message to the user when the user receives the text message. Open the browser, enter the URL in the address bar, download the image stored in the main directory of the web server, and you can view the experimental results. The displayed picture results are shown in Figure 4. The system will frame the moving objects in the camera's field of view and record the time of the moving objects.
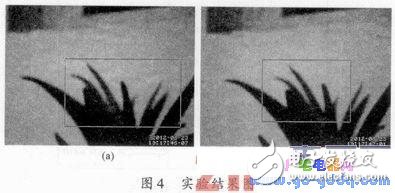
This paper designs a motion detection system with ARM11 as the core chip and embedded Linux as the operating system. The background difference method and the interframe difference method are combined as the core algorithm. And combined with the GSM module, has achieved the purpose of monitoring unattended, the experimental results have achieved the intended purpose, the system is small in size, low power consumption, low cost, easy to use, flexible, and can be used in the home environment Or a place such as a private office. Has a good market prospects.
ZTTEK Batteries, For 5G backup base station .Customize the lithium ion battery packs according to the application and product requirements of the customers.
Lithium ion battery integration requires a special set of skill and expertise to optimize the performance and battery life.ZTTEK Batteries , using the most advanced technology delivers the best quality battery packs.
Our batteries are safe to use, better performance, higher shelf life and a very low maintenance cost.
48V100Ah Lithium Ion Battery,Lithium-Ion Battery For Home Backup Electricity,Lithium Ion Battery 48V 100Ah,48V Lithium Iron Phosphate Battery
Jiangsu Zhitai New Energy Technology Co.,Ltd , https://www.zhitainewenergy.com